Streembit aims to implement a free, open source, secure, decentralized, peer to peer communication system to protect your real time communication. Streembit addresses issues primarily related to safety, politics, security, privacy, economy, and the Internet of Things all while complying with standards.
Security and Privacy
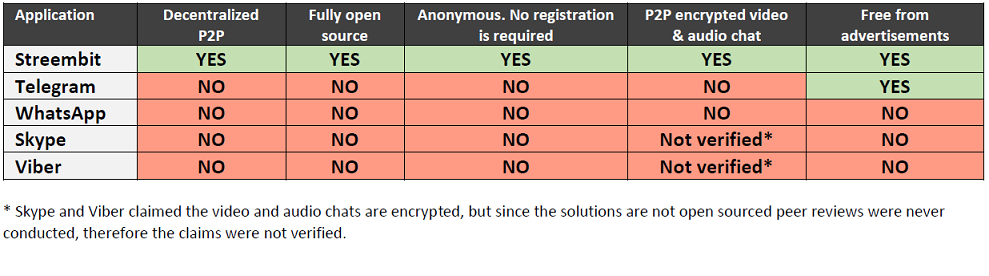
Current communication systems like Skype, Viber, and Telegram are centralised solutions, meaning there are central servers operating between the users. Most of these popular systems also use a closed source, proprietary software. Users have no idea how their data is handled, what is actually decrypted, where their data is forwarded to, or who is listening to the communication.
Because these centralised solutions are not open source, they have never been peer reviewed. There is no way to tell whether or not they implement a security backdoor, or if they are even secure to begin with. We propose a fully open source system so cryptographers, security experts, and software professionals can peer review it, and verify that it complies with security standards.
Vulnerability to hacking is another security issue. Over the years, the credit card numbers, social security digits, and personal details of tens of millions of individuals have been stolen from centralised servers. Our solution is a fully decentralised peer to peer (P2P) system, which has no need to store the mass amounts of client information and sensitive data in a central server as centralised systems do.
Occupations
There are certain occupations where client confidentiality is of utmost importance. These include, but are not limited to, journalists, lawyers, accountants, and doctors. The clients of these professionals understandably want end-to-end, fully encrypted, and uncompromised security. We believe a decentralised peer-to-peer system is well suited to provide users with this level of security and confidentiality.
Internet of Things
Streembit manages device discovery as well as authentication, access control, and provisioning of devices without using a centralized authority server. The system facilitates device discovery and device control in a peer to peer manner. For many IoT use cases a decentralized P2P network topology is the most secure, robust, scalable, and reliable method of operation.
Streembit manages Internet of Things devices without the need of expensive, corporate owned, third party, proprietary centralized cloud platforms. Centralized corporate owned cloud is certainly an easier way to build out IoT platforms; however, the owners and authorities of these topologies have an influence upon the network and can exploit it. They can ban devices, spy on devices, and compromise the data integrity of the devices. In fact, the government can order the cloud owners to do all of these things.
In the near future, the doors, air condition units, and security system of your home will be fully internet connected. You will be able to control your home automation system from your mobile phone. It is essential that only you can control your IoT devices. Streembit excludes third party service and cloud providers from the ecosystem to give full control of the devices to the end users. The Streembit IoT implementation is based on open standards.
Politics
Incoming communication legislation such as the UK Investigatory Powers Bill, as it is explained here and here, will make it impossible to preserve privacy and secure communication using a centralised client-server solution. Any solution that requires a central server will be subject to the proposed laws. Currently, by definition, all web sites, cloud services, and client-server systems are centralised solutions. Therefore, they will all be forced to incorporate a master encryption key and decrypt the client’s communication upon the request of the government.
It is safe to assume that measures like the UK Investigatory Powers Bill could become the standard. The majority of recent US presidential debates have been about security and terrorism, which may advance the enforcement of such laws around the world. Key disclosure laws are already enforced in certain countries. Business, centralised, cloud based, and client-server solutions must comply with these laws and regulations. Despite the best intention of proprietary software companies such as Apple the government will press businesses to comply and give up their customers’ data.
On the other hand, individuals can’t be forced to divulge their encryption passphrase. Community driven open source P2P systems such as Streembit, which ecosystem includes no centralised server nor a service provider cannot be subject of subpoenas.
We believe peer to peer (P2P) is the only solution to preserve privacy. Individuals won’t be subject to these proposed laws. Streembit users who communicate with family members or friends via video chat, hold a team meeting, or transfer data using our decentralised system won’t have to surrender their local data to the government.
Safety
Human right activists, dissidents, and citizens who stand up against totalitarian states and undemocratic policies also need a secure communication tool. Oppressive regimes are even cracking down on critics beyond their own borders. A decentralised peer to peer system, in which the communication is fully encrypted between the users, preserves privacy without using a central server, and keeps the data safe from oppressive regimes.
Economy
Decentralisation addresses several major system and business requirements. Decentralised systems are scalable; in fact they become more stable if there are more active users. This means that no expensive cluster servers are needed to run a decentralised system. The peers make up the system with their home and office computers, tablets, and mobile devices.
Decentralised systems are the composite of their peers, and are always available as long as at least two peers are connected. On the other hand, centralised systems require expensive load balancers, and even more costly data centers across geographical regions to provide high availability. A decentralised P2P system makes centralised high-cost server infrastructures obsolete.
Standards
Streembit aims to comply with open security and communication standards. The compliance is verifiable via peer review of the Streembit open source system. Streembit is built on FIPS, IETF and W3C security; data and communication standards such as JWT, JWS, WebRTC, as well as the latest planned and actual standards from W3C Web of Things initiative. The system uses recommended curves for the ECDSA and ECDH elliptic curve cryptography functions.
Mitigate the risk of inside job hacking
Many experts suggest that the majority of hacking directed against companies actually stems from insiders within the companies themselves. Centralized systems will be always vulnerable to dishonest employees. It is no wonder that over the years the credit card details, social security numbers, and personal details of tens of millions of individuals have been stolen from centralised servers.
Decentralized systems address this issue by not storing a large amount of sensitive information in one central place, and securing the stored data with cryptography functions to make it visible only to the owner of the data. Such encrypted data isn’t useful for cyber criminals, and because there is no way to crack strong encryption with brute force attacks; there is very little incentive for cyber criminals to steal data from a decentralized system.
Check out other open source projects I have contributed. You can contact me at tzpardi@streembit.com if you have any questions or comments.